Mobile Security
Phone technology has transformed dramatically in the last 10-15 years. Not only can we call people, but most if not all phones are capable of connecting to the internet. And we all know what that means…bad stuff can happen. It’s time we started to look at our phones as not just arbitrary devices we have to communicate, but as points of potential compromise. Hopefully after reading this article you’ll have a better sense of what threats are out there and how to better protect yourself on your mobile device.
Most of the Same
Modern phones are just computers will satellite calling capabilities. That’s literally it. It functions in many similiar ways to a laptop or a PC. You have programs/apps, an operating system and internet access at the very least. Unfortunately, this opens us up to a lot of the same vulnerabilities we see more traditionally with PC’s or laptops. All a hacker has to do is find that one place where security is lacking and you could potentially be compromised. Let’s explore some common places where we might see points of entry on a phone, and what you can do to keep yourself safe.
The Internet
I think this is probably the most self explanatory. I remember the days when cell phones didn’t have internet, or if they did it cost extra money to use it, so nobody used it haha. This notion of being able to access anything online was only really relevant for laptops and desktops. Now our phones can connect to the internet with ease, and all phones require some type of internet connection to even be able to update their software and do most functions. This means that you can run into a variety of malicious content on the internet through your phone.
Adware, spyware and malware are all still fair game, even on mobile devices. All it takes is a visit to the wrong website, and you could inadvertently download one of these viruses. For the most part, I’d say it is pretty hard to get one of these on your phone unless you have poor cyber hygeine. It can be tempting to click on all the things your phone screen is showing, but visting legitimate sites and downloading from trusted sources reduces risk.
Application/Software Updates
While it’s great to think that downloading something bad on the internet is going to be the only way of compromise for most attacks to occur, your existing apps and operating system are probably going to be the #1 factor in your device being compromised. We’ve all gone through app and software updates on our mobile devices. They can be quite annoying and potentially take a long time to download. However, this is going to be the main defense in mitigating most cyber attacks for your phone. First let’s talk about applications.
Here’s a sample scenario of how you might start your day: In the morning, you may take a quick glance at Instagram’s app and post a story. Then you might pull up the weather app to see the weather for the day. Next, you open Google Maps to find out how to get to a certain location you’re meeting a friend at. Each app has their own specific ways of functioning, and most importantly, their own ways in how they are securing the data they are permitted to see (more on this later).
Unlike browsing the web for these exact activities on a normal desktop, each of these apps exist independently on your phone. This means that each app has their own coding structure that could potentially be vulnerable to some exploit if there are security holes in it. So while the Instagram desktop website may be hard for a hacker to bypass, the phone app itself could be easier to take advantage of. This is why it is important to update your phone apps as soon as they become available. You may not like the new interface the app slapped onto it for the update, but you can guarantee there are security updates included in the release that fixes some security hole that existed in the prior version.
This also goes for phone software updates in general. If a hacker is able to find an exploit for a certain software vulnerability in the phone, who cares about what app is vulnerable. They potentially hit the jackpot and could take total control over the phone itself if the attack is crafted properly. This article details some of the most recent iphone vulnerabilities that security researchers have found. Probably the most valuable asset to a hacker is time. And trust me, the most notoriuous of them have a lot of it. There are countless hours poured into researching if these operating systems and applications have vulnerabilities in them. If we’re able to stop/frustrate them by simply updating the app/sofware, why wouldn’t we do so?
Of course not everyone likes to play it safe, even if you aren’t a hacker. You may just be interested in modifying your phone to see how much customization you can implement from a creative standpoint. This is where you might run into trouble…
Rooting and Jailbreaking
If these terms aren’t familiar to you, it’s because that’s by design of the companies that create our mobile devices. If you are familiar with these terms, you’ve potentially done this to one of your iphones or androids in the past. I’ve definitely done it. But what is rooting and jailbreaking? More importantly, why does this matter?
Right now if I asked if you had complete control over your mobile device, what would your response be? Yes or no? For most normal iphone or android users, the question might sound a bit odd. Of course you have control over your device. You control what gets downloaded, what you share and everything else on your mobile device. If you’re more tech savy, you definitely would not agree with the previous statement.
The short objective answer is no, you do not control everything that happens on your phone. This is for good reason. Most people do not need to tap into the full capabilities of the operating system running their iphone or android, and probably never will. With jailbreaking and rooting, this becomes possible. The added benefits of gaining access to these parts of your phone are based on subjective use cases (i.e overclocking the GPU, UI customization, adding third party app repositories, etc.). However, when we root or jailbreak our mobile devices, we effectively bypass certain security controls that the operating system has in place. Let’s take downloading apps as an example.
When you download an app, it’s coming from either the Apple or Google Play store. All apps that make it onto those platforms are vetted by each company, meaning that not anyone can just upload an app with malware on it to the store. There’s a proccess for each of these apps to be added for public downloads. This handled automatically by Apple and Google, so there isn’t anything individual users have to do. You download the app and that’s it.
In contrast, let’s say that you have a rooted or jailbroken phone. Instead of using the Apple or Google store to find apps, it is now possible to download apps through different hosts. Third party app hosters make plently of modified versions of apps available for people to download. Obviously, these are not vetted by Apple or Google, which means that someone could easily upload an app that is secretly malware/spyware/adware in disguise. Once you download the app, that could be an automatic compromise.
Needless to say, I don’t think jailbreaking or rooting will be a problem for most users, but this is just another avenue for hackers to potentially get ahold of your device. I don’t recommend it, but if you do decide to root or jailbreak your phone, please make sure you’re as safe as possible. There are forums and guides out there that you can follow that are legitimate, and will guide you in the right direction.
App Permissions
Ah good ol’ app permissions. They’re the reason why apps have information such as your GPS location, phone contacts and mic/camera access. Although these permissions seem like a no brainer when it comes to what these apps need, they too present risk. Let’s pretend that the app you’re using is pretty secure. This means that there are little to no major vulnerabilities that can be exploited practically by a hacker. However, there are still privacy concerns that you may need to be weary of.
Data privacy concerns have been at the forefront of cyber security for quite some time. Every so often you’ll see Facebook, Google or (enter your favorite tech company) in the news about some kind of data privacy violation or change that affects its users. This goes far beyond what’s just on your phone. When it comes to making apps, phones need to ask for your permission to access certain kinds of information it can use for certain features (i.e. the camera). This is where things get dicey.
If you have an Iphone, I’m sure you’ve seen this screen:
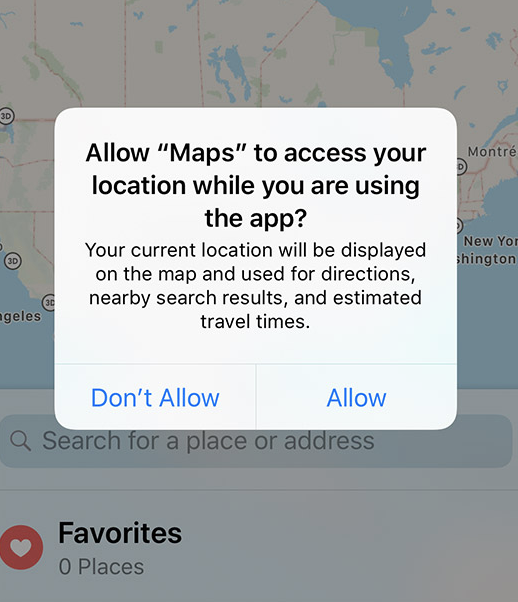
You can replace “Maps” with any other app that uses your location. If you click “allow,” you have essentially given the app permission to see where you are in the world. This goes for any other permission that you allow. Apps appear to have more invasive permissions that they immediately need as compared to their desktop equivalent. For example, facebook the website does not require full access to your photos on your local desktop in order for you upload something. However, the app does require access to all of your photos on your phone.
Apple has more or less been upfront about which permissions it needs when an app is requesting them for use. Android has not always followed suit. Luckily, android has changed their permissions scheme as of version 6.0. In previous versions, the user would have to allow ALL permissions in order to use the app, which is problematic. Both companies in general have significantly improved the way in which they allow users to control which permissions the apps are allowed to have. They’ve even gone as far as only allowing access to certain data while your using the app, and not have access when you aren’t.
It’s very important to look and see which permissions are needed for certain apps. For example, if you’re downloading a calculator app, there’s no good reason it needs to know your location and/or contact information. As we deal with more complicated applications, we need to do our due diligence in understanding what is happening with our data on these apps. I’m willing to bet none of us have ever read the privacy policy that companies make available. I sure as hell haven’t. This creates an implicit trust that we give to companies in how they are managing our data. That trust is built around the fact that we’re allowing companies to not only store our data, but use it elsewhere because we clicked “Yes, I agree.” Even though we’re more concerned with hackers gaining this information through exploiting the app, third party companies that have our data are also potential points of compromise.
Hopefully after reading this article you have a better sense of mobile security from a practicial standpoint. There are many layers involved in protecting our data on our phones, but if we can do the bare minimum, we’ll be able to thwart most attacks. Obviously, there are more ways than described in this article to do so, but that’s where the outside research part comes in. Good luck!
Thank you for reading!
